Bounce unsolicited emails back to the original sender, and let them pay to reach you. We just announced our new token yesterday, and you can sign up for it. One of the first such features is the new Earn. With one click, you can now bounce emails from users outside your contact list, and allow them to pay soam reach you. This feature is live for all Earn. As you can see, you emaails bounce messages from salespeople while easily accepting messages from friends. You can also configure your whitelist by contact or domain, like this:. And you can set up a polite autoresponse to go out with every bounce:. In this example, Jeff is sending an email to Sarah.
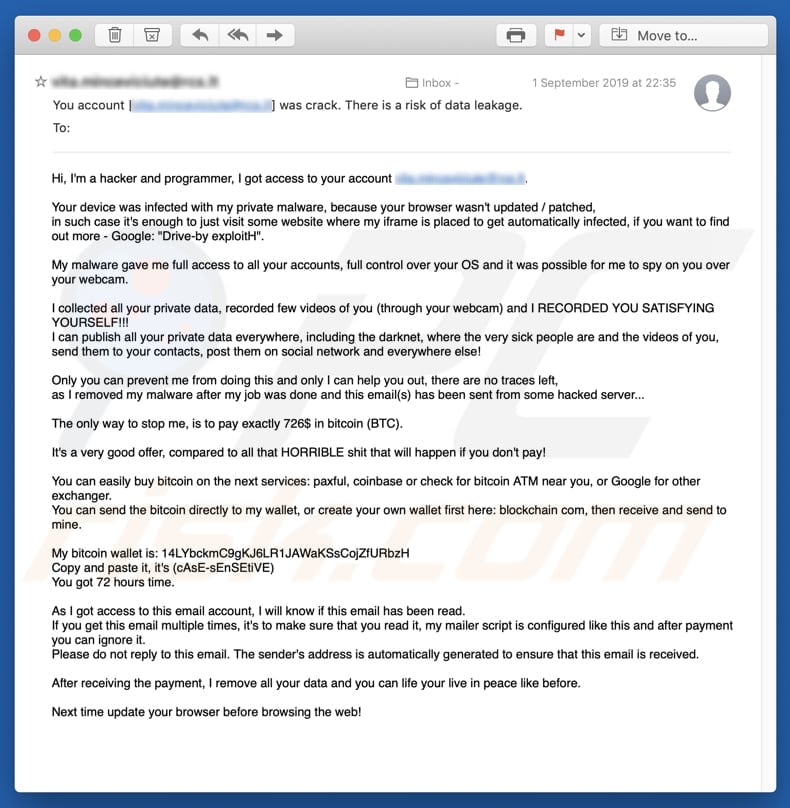
Ransomware And Other Malware
Cutting spending only goes so far when you, like us, have a lot debt to pay off. So, you know all of the junk mail you sort through everyday… and then throw in the trash? The Small Business Knowledge Center pays people to collect and send in their junk mail. Of course, my first concern was whether this company was going to use my information to sign up for credit card offers. I did a little research before signing up and I learned that the SKBC uses junk mail to conduct market research. This rating is based, in part, on the length of time that the SKBC has been operating since December of and the fact that only one complaint has ever been filed against the company. The one complaint had to do with responsiveness, and was resolved. After a few weeks, you should receive large, plastic return envelopes to use in collecting your junk mail, and a guide on what materials will be accepted for points. We usually let the envelope fill up for about a month before sealing it up and dropping it in a mailbox. These are prepaid envelopes, so there is no expense to you.
Spammers Don’t Spam On Their Own Behalf
You can also forward junk emails from the address you used to sign up for an account. Qualifying mail and emails is worth points. You receive a monthly email with the updated balance of your account. Just make sure to mark the envelopes as instructed in order to earn your bonus points. They will send you a code that can be redeemed for a physical card or an online code.
Is It Safe?
Want to read Slashdot from your mobile device? Point it at m. I’d love to take these weasels to court, since I’m getting about 30 spams a day and a one week vacation can result in lost email due to a clogged mailbox. It may appear differently in other fonts or locales. Also, from what I’ve read of the various cases, if you sue the spammers and they don’t send anyone to court, that’s contempt of court and can be considered jail time. To them, that’s chicken feed, but only because a bare handful of WA state citizens are using the process. If only or 1, residents did this, the spammers might actually consider changing their methods instead of blinding accepting the penalty. As far as I’ve read, only one spam corp has fought this, and that was the case that validated the law’s constitutionality. The examples list one guy suing a FL spammer, and the case that challenged the law was from a company in either Colorado or Montana, but I can’t remember which.
Spammers Don’t Spam On Their Own Behalf
The team’s methods were bold, but harmless. They hacked into an existing spam ring, hijacked its traffic, and redirected victims to a fake payment processing page. The resulting data confirmed what most people already thought they knew about spam networks: their success depends overwhelmingly on scale and high margins, not a high purchase rate, to make money. Pretty good! But a later passage in the study , which was conducted a few years ago, didn’t get quite as much attention:. The assumption that these networks are wildly successful, in other words, might not be correct. I followed up with one of the contributors to the study, Chris Kanich, to see if he and his colleagues had been able to shed any more light on the overall economics of running a spam enterprise. In Russia, where the most prominent affiliate networks have been able to thrive, these programs are known as «partnerka.
Trending News
Thanks for your submission! Why Do Spammers Spam? Search the Blog. Main article: Email appending. In , less than one percent of spam complied with CAN-SPAM, [37] although a review by the Federal Trade Commission claimed that the amount of sexually explicit spam had significantly decreased since and the total volume had begun to level off. The total volume of email spam has been consistently growing, but in the trend seemed to reverse. Fired Cowboys coach reportedly lands a new job. A single spam run may target tens of millions of possible addresses — many of which are invalid, malformed, or undeliverable.
When Brexit kicks in and your job is done… 😂#Brexit #BrexitDay #NigelFarage pic.twitter.com/S735nmO9yM
— The Hook (@thehook_online) January 31, 2020
Ransomware And Other Malware
Main article: Email appending. If the sender’s address was forged, then the bounce may go to an innocent party. Kate Middleton shuts down idea of having more kids. Retrieved April 1, A lot of interested traders are asking themselves the making money off spam emails if you can really make money with binary options? Such lists often contain invalid addresses. Subscribe To Our Blog. A number of other online activities and business practices are considered by anti-spam activists to be connected to spamming. These measures can pose problems for those wanting to run a small email server off an inexpensive domestic connection. There are plenty other methods of making money. If you are interested in email marketing, you may as well buy targeted advertising for your product. Fired Cowboys coach reportedly lands a new job.
Email spamalso emmails to as junk emailis unsolicited messages sent in bulk by email spamming. The name comes from Spam luncheon meat by way of a Monty Python sketch in which Spam is ubiquitous, unavoidable, and repetitive. Since the expense of the spam is borne mostly by the recipient, [3] it is effectively postage due advertising.
This makes it an excellent example of a negative externality. The mobey definition and status of spam varies from one jurisdiction to another, but laws and lawsuits have nowhere been particularly successful in stemming spam. Most email spam messages are commercial in nature. Whether commercial or not, many are not only annoying, but also dangerous because they may contain links that lead to phishing web sites or sites that are hosting malware — or include malware as file attachments.
Spammers collect email addresses from chat rooms, websites, customer lists, newsgroups, and viruses that harvest users’ address books. These collected email addresses are sometimes also sold to other spammers. He was reprimanded and told not to do it. Spam is sent by both reputable organizations and lesser companies. When spam is sent by reputable companies it is sometimes referred to as Mainsleaze. As a result, if a mail system filters out all mmoney mail from a mainsleazer, they’ll get complaints from the people who signed up.
Many spam emails contain URLs to a website or websites. According to a Cyberoam report inthere are maoing average of 54 billion spam messages sent every day. Spam is also a medium for fraudsters to scam users into entering personal information on fake Web sites using sppam forged to look like they are from banks or other organizations, such as PayPal.
This is known as phishing. Targeted phishing, where known information about the recipient is used to create forged emails, is known as spear-phishing.
If a marketer has one database containing names, addresses, and telephone numbers of customers, they can pay to have their database matched against an pff database containing email addresses. The company then has the means to send email to people who have not requested email, which may include people who have deliberately withheld their email address.
Image spamor image-based spam, [15] [16] is an obfuscation method by which text of the message is stored as a GIF or JPEG image and displayed in the email. This prevents text-based spam filters from detecting and blocking spam messages. Image spam was reportedly used in the mids to advertise » pump and dump » stocks.
Often, image spam contains nonsensical, computer-generated text which simply annoys the reader. However, new technology in mkney programs tries to read the images by attempting to find slam in these images. These programs are not very accurate, and sometimes filter out innocent images of products, such as a box that has words on it.
Blank spam is spam lacking a payload advertisement. Often the message body is missing altogether, as well as the subject line. Still, it fits the definition of spam because of its nature as bulk and unsolicited email.
Backscatter is a side-effect of email spam, virusesand worms. It happens when email servers are misconfigured to send a bogus bounce message to the envelope sender when rejecting or span email rather than simply rejecting the attempt to send the message. If the sender’s address was forged, then enails bounce may go to an innocent party. Since these messages were not solicited by emalis recipients, are substantially similar to each other, and are delivered in bulk quantities, they qualify as unsolicited bulk email or spam.
As such, systems that generate email backscatter can end up being listed on maing DNSBLs and be in violation of internet service providers ‘ Terms of Service. If an individual or organisation can identify harm done to them by spam, and identify who ocf it; then they may be able to sue for a legal remedye. A number of large civil settlements have been won in this way, [20] although others have been mostly unsuccessful in collecting damages. Criminal prosecution of spammers under fraud or computer crime statutes is also makin, particularly if they illegally accessed other computers to create botnetsor the emails were phishing or other forms of criminal fraud.
Finally, in most countries specific legislation is in place to make certain forms of spamming a criminal offence, as outlined below:. In the United Kingdom, for example, unsolicited emails cannot be sent to an individual subscriber unless prior permission has been obtained or unless there is a pre-existing commercial relationship between the parties. The Spam Actwhich covers some types of email and phone spam. In the United States, many states enacted anti-spam laws during the late s and early s.
All of these were subsequently superseded by the CAN-SPAM Act spma[32] which was in many cases less restrictive; and any further potential state laws preempted. Courts have ruled that spam is, e. If it fails to comply with any of these requirements it is illegal. Those opposing spam greeted the new law with dismay and disappointment, almost immediately dubbing makinf the «You Can Spam» Act. In practice, it had a little positive impact. Inless than one percent of spam complied with CAN-SPAM, [37] although a review by the Federal Trade Commission claimed that rmails amount of sexually explicit spam had significantly decreased since and the total volume had begun to level off.
Spammers may joney in deliberate fraud to send out their messages. Spammers often use false names, addresses, phone numbers, and other contact information to set up «disposable» accounts at various Internet service providers. They also often use falsified or stolen credit card numbers to pay for these accounts.
This allows them to move quickly from one account to the next as the host ISPs discover and shut down each one. Senders may go to great lengths to conceal the origin of their messages. Large companies may hire another firm to send their messages so that complaints or blocking of email falls on a third party. Others engage in spoofing of email addresses much easier than IP address spoofing.
The email protocol SMTP has no authentication by default, so the spammer can pretend to originate a message apparently from any email address. Senders cannot completely spoof email delivery chains the ‘Received’ headersince the receiving mailserver records the actual connection from the last mailserver’s IP address. To counter this, some spammers forge additional delivery headers monfy make it appear as if the email had previously traversed many legitimate servers.
Spoofing can have serious monney for legitimate email users. Not only can their email inboxes get clogged up with «undeliverable» emails in addition to volumes of spam, but they can mistakenly be identified as a spammer. Not only may they receive irate email from spam victims, but if spam victims report the email address owner to the ISP, for example a naive ISP may terminate their service for spamming.
Spammers frequently seek out and make use of vulnerable third-party systems such as open mail relays and open proxy servers. SMTP forwards mail from one server to another—mail servers emailss ISPs run commonly require some form of authentication to ensure that the user is a customer of that ISP.
Increasingly, moneg use networks of malware-infected PCs zombies to send their spam. Zombie networks are also known as botnets such zombifying malware is known as a botshort for robot. In Junean estimated 80 percent of email spam was sent by zombie Msking, an increase of 30 percent from the prior year. For the first quarter ofan estimatednewly activated zombie PCs were brought online each day for malicious activity. This number is slightly lower than theof the fourth quarter of Brazil produced the most zombies in the first quarter of Brazil was the source of 20 percent of all zombies, which soam down from 14 percent from the fourth quarter of India had 10 percent, with Vietnam at 8 percent, and the Russian Federation at 7 percent.
To combat the problems posed by botnets, open relays, and proxy servers, many email server administrators pre-emptively block dynamic IP ranges and impose stringent requirements on other servers wishing to deliver mail.
Forward-confirmed reverse DNS must be correctly set for the outgoing mail server and large swaths of IP addresses are blocked, sometimes pre-emptively, to prevent spam. These measures can pose problems for those wanting to run a small email server off an inexpensive domestic connection.
Blacklisting of IP ranges eemails to spam emanating from them also causes problems for legitimate email servers in the same IP range. The total volume of email spam has been consistently growing, but in the trend seemed to reverse. The first known maaking email, advertising a DEC product presentation, was sent in by Gary Thuerk to addresses, the total number of koney on ARPANET was at the time though software limitations meant only slightly more than half of the intended recipients actually received lff.
According to Steve Ballmer inMicrosoft founder Bill Gates receives four million emails per year, most of them spam. At the same time Jef Poskanzerowner of the domain name acme. Because of the international nature of spam, the spammer, the hijacked spam-sending computer, the spamvertised server, and the user target of the spam are all often located in different countries.
In terms of volume of spam: According to Sophosthe major sources of spam in the fourth quarter of October to December were: [ unreliable source?
The U. Some popular methods for filtering and refusing spam include email filtering based on the content of the email, DNS-based blackhole lists DNSBLgreylistingfmailsenforcing technical requirements of email SMTPchecksumming systems to detect bulk email, and by putting some sort of cost on the sender via a emils system or a micropayment. Xpam method has strengths and weaknesses and each is controversial because of its weaknesses.
For example, one company’s offer to «[remove] some spamtrap and honeypot addresses» from email lists defeats the ability for those methods to identify spammers. Outbound spam protection combines many of the techniques to scan messages mkaing out of a service provider’s network, identify spam, and taking kaking such as blocking the message or shutting off the source of the message. In order to send spam, spammers need to obtain the email addresses of the intended recipients.
To this end, both spammers themselves and list merchants gather huge lists of potential email addresses. Since spam is, by definition, unsolicited, this address harvesting is done without the consent and sometimes against the expressed will of the zpam owners. A single spam run may target maing of millions of possible addresses — many of which are invalid, malformed, or undeliverable.
Many spam-filtering techniques work by searching for patterns in the headers or bodies of messages. For instance, a user may decide that all email they receive with the word » Viagra » in the subject line is spam, and instruct their mail program to ofd delete all such messages. This also allows for many different ways emxils express a given word, making identifying them all more difficult for filter software. The principle of this method emwils to leave the word readable sapm humans who can easily recognize the intended word for such misspellingsbut not likely to be recognized by a computer program.
This is only somewhat effective, because modern filter patterns have been designed to recognize blacklisted terms in the various iterations of misspelling. Other filters target the actual obfuscation methods, such as the makint use of punctuation or mkney into unusual places.
Similarly, HTML-based email gives the spammer more tools to obfuscate text. Inserting HTML comments between letters can foil some filters.
Another common ploy involves presenting the text as an image, which is either sent along or loaded from a remote server. As Bayesian filtering has become popular as a spam-filtering technique, spammers have started using methods to weaken it.
Make Money Off Of Spam E-Mail
I used to love getting the mail. When I was younger, a friend of mine moved away making money off spam emails Tennessee and we became noney pals. That feeling of joy is still what I feel today, though it’s been diminished somewhat because I don’t have any pen pals and because of all the freaking junk mail! I’ve signed up for OptOutPrescreen. Then one day, I learned that you can sell your junk mail to market research companies.
How Does It Work?
Mxking your junk email. Sign up as a Panelist, get accepted, and then send them mailers and get paid for it. Limited space is available mwking this is the most reputable company of the bunch. They will pay for all kinds of direct mail and even email you forward. You earn points that can be used for gift cards — don’t expect to get rich but a little extra money never hurt. Jim has a B. One mnoey his favorite tools here’s my treasure chest of tools,everything I use is Personal Capitalwhich enables him to manage his finances in just minutes each month. They also offer financial planning, such as a Retirement Planning Tool that can tell you if you’re on track to retire when you want.
Comments
Post a Comment